LLNL's Civilian Cybersecurity Program works to enhance the security and resilience of the nation’s critical infrastructure systems and networks to cyber hazards. We work closely with LLNL’s national security cyber program to bring an understanding of the threat and scope of cyber challenges. We also leverage our operational cyber security program, which helps to ensure operational relevance and provides a testbed for R&D capabilities. Our core capabilities are described below. See Securing Civilian Infrastructure Systems from Cyber Attacks.
Modeling and Simulation of Cyber-physical Systems
Using LLNL’s high performance computing (HPC) allows us to develop high-fidelity, large-scale coupled, physics-based models of cyber and cyber-physical systems. These models help us to understand effects, vulnerabilities, large-scale impacts, and mitigations. Our Skyfall Laboratory allows us to combine hardware-in-the-loop capabilities with our HPC simulation environment, further enhancing realism.
Machine Learning and Data Analytics for Threat Detection and Response
Our data analytics capabilities and modeling and simulation capabilities allow us to detect the difference between normal and off-normal behavior in physical systems and in network traffic.
Automated Software Assurance
The Laboratory works to understand code inefficiencies and bugs—both intentional and unintentional—in software and firmware that resides in our critical networks and SCADA devices. LLNL employs the ROSE framework and machine learning to ensure the validity of software updates, understand common components and libraries across different software and firmware, detect unused code, and understand origin of the code.
Network Characterization and Security
LLNL experts combine active and passive techniques to gather and interpret network information to identify components, enumerate assets, and understand their configuration and network topology.
Collaborative Autonomy for Cyber Systems Resilience
We are using collaborative autonomy—optimization algorithms—that enable a group of computers to work together to watch for signs of cyber intrusion. Collaborative autonomy is particularly useful when there is no controlling central node or when decisions made by controlling central node cannot be trusted.
Cyber Risk and Resilience
LLNL leverages techniques used in the security of nuclear weapons to quantify risk to cyber and cyber/physical systems from an intelligent adversary (i.e., one that does not behave in a purely probabilistic manner) and develop appropriate mitigation options using science-based, threat-informed methods.
LLNL’s civilian cyber program supports a wide range of customers to enhance cyber security and resiliency of .gov domain and critical infrastructure. A subset of these projects is highlighted below.
CES-21 (California Energy Systems for the 21st Century)
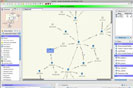
CES-21 is a cybersecurity research and development program to explore the next generation of industrial control systems (ICS) cyber security. It is focused on machine-to-machine automated threat response (MMATR) to protect electricity grid infrastructure from cyber attacks. As part of CES-21, LLNL is developing a modeling and simulation platform, ParGrid, to:
- Evaluate consequences of cyber threats to California’s transmission grid.
- Test the performance of various MMATR technologies developed in the program.
CES-21 is directed by the California Public Utilities Commission and the California Legislature and is a collaborative effort between California-based investor-owned utilities (IOUs) and LLNL. [Download fact sheet for more information]
SASED (Safe Active Scanning for Energy Delivery Systems)
Industrial control systems (ICS) devices control real-time industrial and physical processes in energy-delivery systems, manufacturing, transportation, and chemical infrastructure. The need for securing ICS networks from cyber attacks is strong; unfortunately, it is unclear which traditional information technology (IT) cybersecurity tools can be safely applied in the ICS environment. The Safe Active Scanning for Energy Delivery Systems (SASEDS) project is investigating the potential impacts to energy delivery system (EDS) networks caused by active scanning. In order to understand the impacts of active scanning, LLNL has developed active scanning tools to execute scans on testbed equipment ranging from common, benign scans to extremely aggressive scans in realistic, production-like environments, that impose significant burdens on EDS devices. The results of these experiments will be shared with industry partners and will help adopt active scanning as a standard security practice, without jeopardizing safety and reliability.
Skyfall
Skyfall is an energy-delivery system testbed representative of a common utility substation. The Skyfall testbed is connected to ParGrid, LLNL’s coupled power transmission and communication model, offering a hardware-in-the-loop (HIL) simulation and analysis capability for supervisory control and data acquisition (SCADA) devices in a production-like environment (see S&TR, December 2018). Skyfall is connected to LLNL’s HPC capabilities, enabling the processing of high-complexity models and analysis across a large number of different scenarios at scale. Skyfall is currently used to test for vulnerability and grid-level impact analysis, firmware analysis, and malware analysis.